Thank You!
BSides Ottawa 2019 has reached it’s end state! We would like to extend exactly one parsec of thank yous to all humanoid / bipedal lifeforms involved!
2020 is BSides Ottawa’s 10th anniversary, and planning is underway. Stay tuned and reach out – we’re made out of people!
Re: Re: Re: Fwd: (Was:) Re:
Brookstreet Hotel
Kanata, Ontario, Canada
Earth, Milky Way
Universe Seed 613095634905719
Thursday, November 28th
Friday, November 29th
Registration opens November 28th at 8:00am.
BSides Ottawa 2019 starts in

About BSides Ottawa
BSides Ottawa is a grassroots-driven conference that provides an open platform for security experts, industry professionals and everyone with an interest in cyber security to share their ideas, questions, insights and research, and to create trusted relationships with members of the National Capital Region cyber security community from the public and private sectors.
Security BSides is a global phenomenon. From SecurityBSides.com:
Each BSides is a community-driven framework for building events for and by information security community members. The goal is to expand the spectrum of conversation beyond the traditional confines of space and time. It creates opportunities for individuals to both present and participate in an intimate atmosphere that encourages collaboration. It is an intense event with discussions, demos, and interaction from participants. It is where conversations for the next-big-thing are happening.
Our Speakers
The call for papers has closed, and 2019 was a record year once again! We would like to gratefully acknowledge each and everyone who volunteered to speak at BSides Ottawa – without you there would be no show!
See the speakers page for the full line-up.
Capture the Flag, Training and Villages
Test your mettle in casual and competitive capture the flag, practice lock picking, jump into free security training and explore IoT and RF technology hacking!
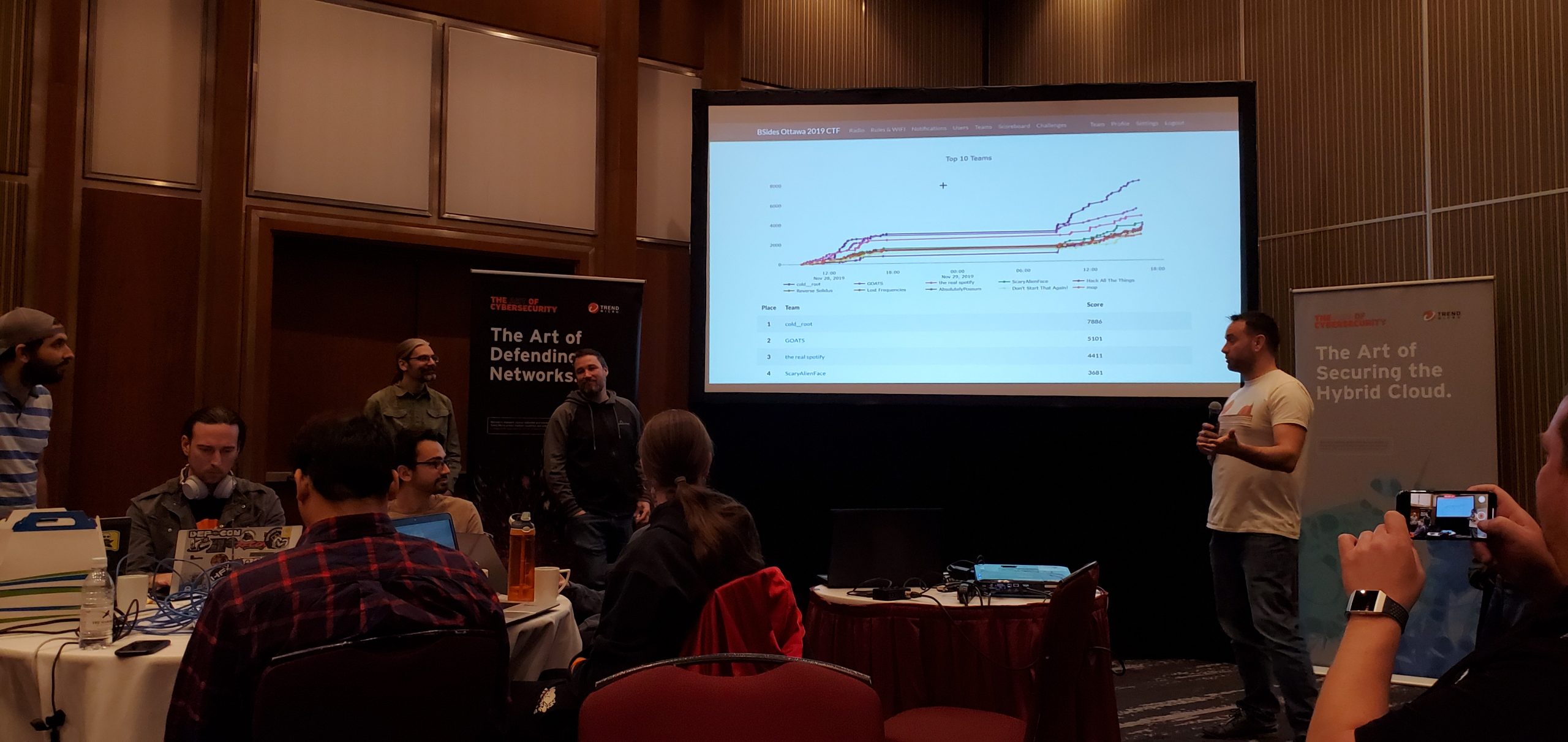
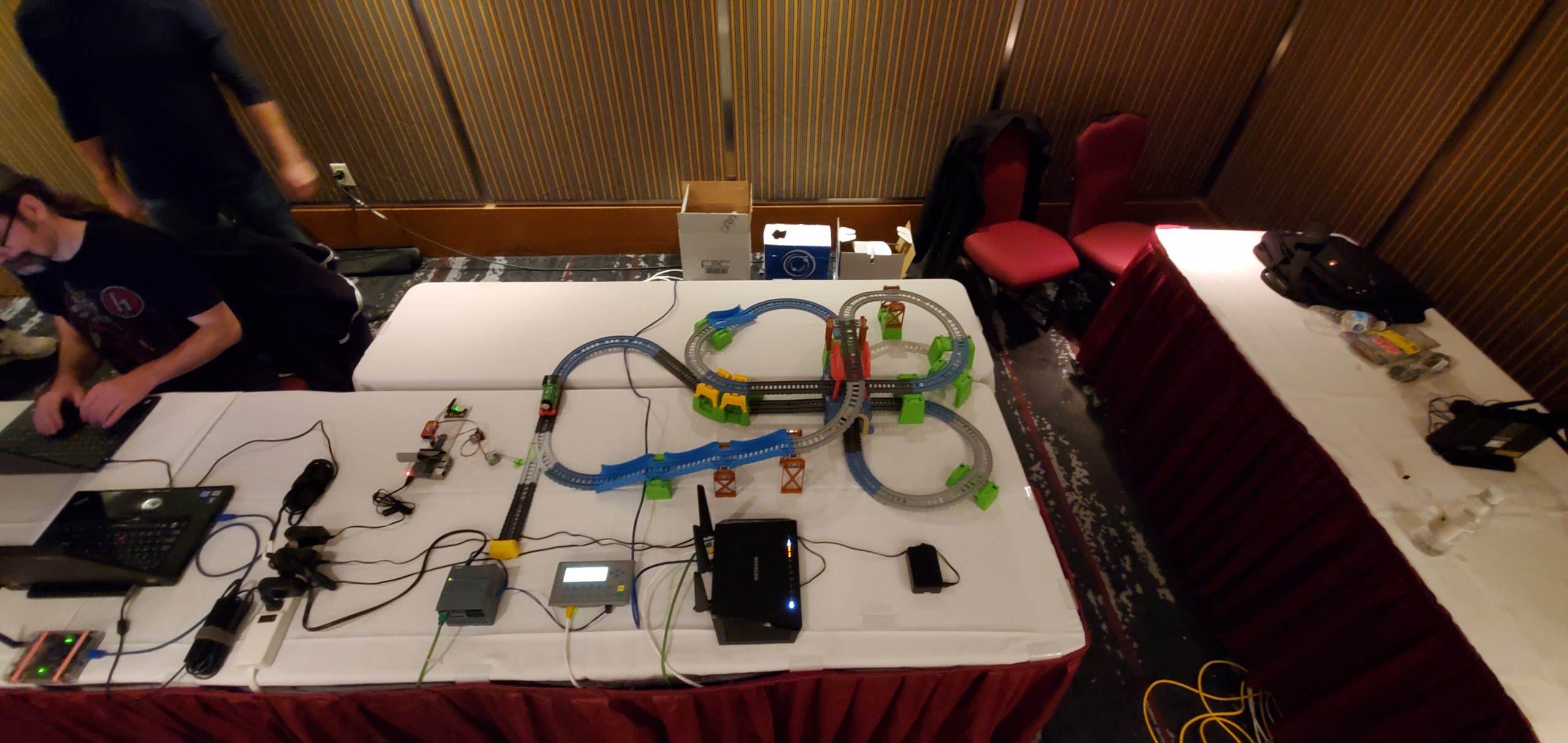
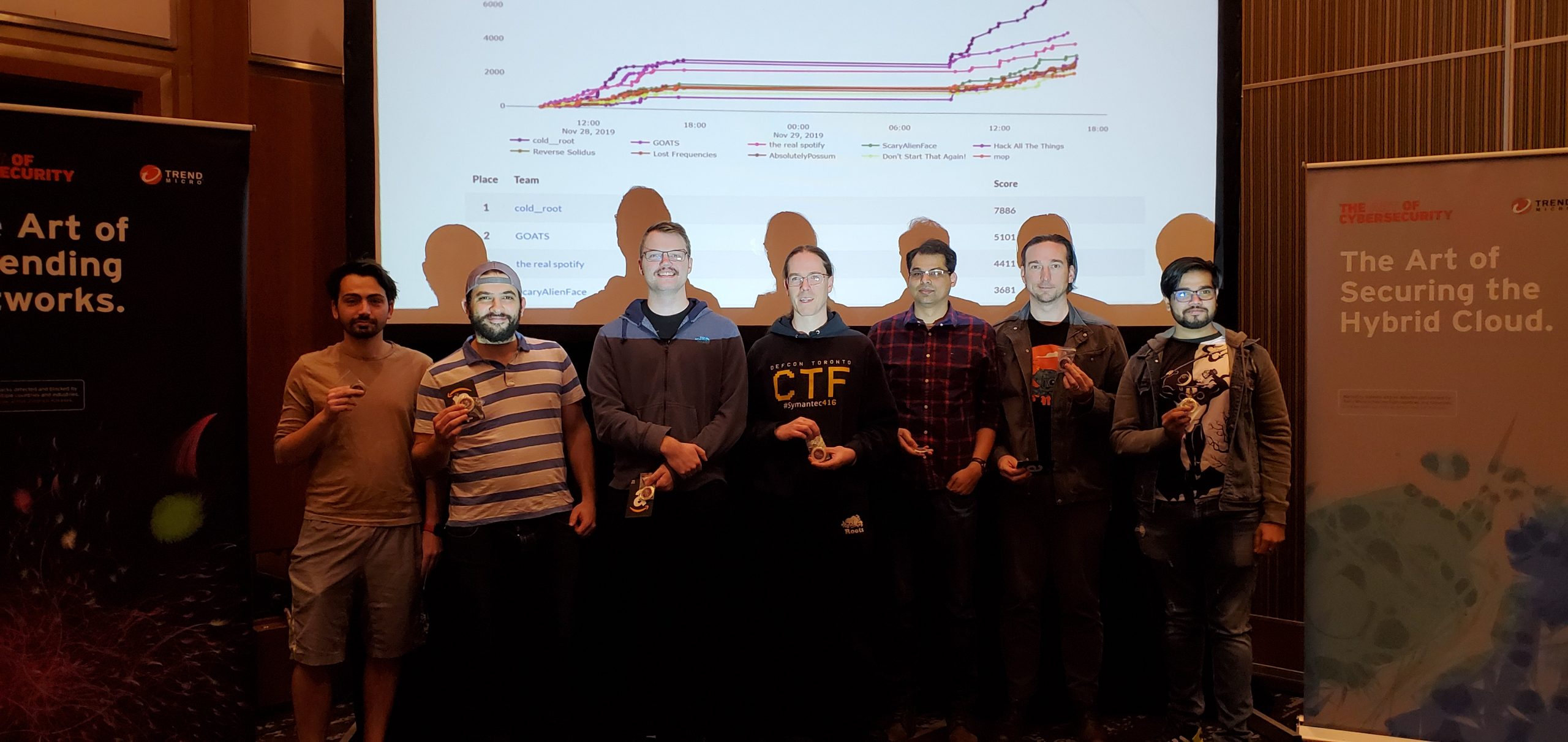
CTF by Xanthus Security
Lockpick Village by TOOOL Ottawa
Application Security Training by OWASP Ottawa
Fortinet Fast Track – Constructing a Secure SD-WAN Architecture
IoT Village created by ISE, presented by Epyc Security & Loudmouth Security
RFID Village by Loudmouth Security
See the Things to Do page for the full lineup!
Presentation Schedule
Day 1
- 08:00 - 09:00
Registration and Networking
Registration and open networking will be between 8am and 9am on days 1 and 2.Social NetworkingWhereMain Venue Area  09:15 - 10:00
09:15 - 10:00Opening Keynote - Machine Learning applied to Cyber Security … This time it’s different?
By Major James Lindsay, MASc, CISSP Chief Architect and Engineer – Endpoint Security, National DefenceMachine learning has gained a lot of hype and has become a buzz word in the last couple of years, and purports to solve many of the challenges facing the cyber security community. However, there has been many hype cycles that have never delivered. This presentation will cover what recent advances has occurred in Machine Learning, what do these advances mean to the cyber security community, what changes need to be made to cyber risk assessments, how can one “hack” Machine Learning algorithms and what are the geopolitical events that could drive the direction and funding of Machine Learning in the foreseeable future.Artificial IntelligenceMachine LearningWhereSpeakers Hall- 10:00 - 10:15
Coffee Break
Perk up and have a snack!Social NetworkingWhereMain Venue Area - One of the main advantages that cyber defenders have over attackers is inside knowledge of their environment. Well, at least they're supposed to. It turns out that many organizations don't have that inside knowledge; the full picture of their IT environment. Without it, cyber defenders are hard pressed to hold onto the high ground; the battlefield is levelled. If an attacker gains access to the network (and is detected), a race condition is started to see who can discover vulnerabilities first and exploit or mitigate them. There is a lot of talk about "just doing the basics" to prevent such attacks and bolster your cybersecurity posture. Unfortunately, "the basics" aren't always easy. During this talk, we'll take a look at three basic – but not necessarily easy – steps to greatly improve your security posture: illuminate your environment, validate your vulnerabilities, and internalize external threats. Getting a handle on these processes and associated tools (demos included!) can help cyber defenders maintain – or regain – the high ground.Cyber OpsWhereSpeakers Hall
 11:00 - 12:00
11:00 - 12:00Securing the Tactical Edge
By Dr. Lawrence Dobranski, P.Eng. Managing Principal Engineer, Catalone IT Security Inc.The tactical edge is an emerging domain in our new borderless computing environment. With the widespread adoption of cloud services, the term tactical edge is used to describe the delivery of the service to the end-user, and the security controls that must be present to ensure that the desired level of residual risk is not exceeded from one end of the IT solution to the other end. Traditionally, information security has focused on the confidentiality of information. With the advent of cloud technology, this has shifted to the tactical edge requirements of availability and integrity of data. This presentation will introduce the tactical edge in the cyber mission assurance environment. It will examine the challenges of continuous compliance and will describe how decentralized, local autonomous deployments, that are usually peer-to-peer or device-to-device, can be secured. It will explore the need to develop new security models to address the challenges of this environment, drawing upon examples from the Internet of Things and low bandwidth, low quality of service connections.Autonomous SystemsComplianceInternet of ThingsWhereSpeakers Hall- 12:00 - 13:00
Lunch
For paid ticket holders lunch will be served.Social NetworkingWhereMain Venue Area  13:00 - 13:45
13:00 - 13:45Keys Under Doormats: Problems and Solutions for Storing Credentials in Web Applications Securely
Encryption keys and passwords are truly "keys to the kingdom." Acquiring them allows attacker to open all kinds of doors, and yet developers are often careless about how they handle them. We often see password and keys hardcoded in the application source, stored with minimal obfuscation in configuration files, and in plaintext in databases. As a result they fall victim to reverse engineering, and software vulnerabilities such as Path Traversal, XXE, Local File Inclusion, and others. To help mitigate that we review right and wrong ways of storing credentials in an application, and discuss best practices for storing them, such as using keystores. Once your secrets are properly secured, however, there is a big remaining issue - how do you secure the "key that secures other keys", the Key Encrypting Key (KEK)? Would it not be vulnerable to the same issues we just tried to solve with keys and passwords? In our presentation we discuss preferred ways for securely storing KEKs, from hardware to software, and their relative costs. We conclude by proposing several low cost ways for storing KEKs that any application can afford to implement and offer an open source library that helps achieve that.Application SecurityEncryptionWhereSpeakers Hall 13:45 - 14:30
13:45 - 14:30Continuous Compromise: How Attackers are Targeting Cloud-Based CI/CD Pipelines and Deployments
By Jamie Baxter Principal ConsultantAs DevOps continues to transform organizations and the use of cloud services becomes ubiquitous, it’s no surprise attackers (and pentesters!) are increasingly targeting the technologies that enable it. We’ll take a tour through a collection of real-life examples and case-studies to explore how vulnerabilities across the CI/CD stack and cloud service deployments are successfully targeted and exploited. Resulting in the disclosure of sensitive information, the co-opting of the build, deployment and orchestration infrastructure and potentially the compromise of the organization itself. But all is not lost, we will conclude with a number of recommendations for teams to raise their security bar without slowing velocity.DevOpsWhereSpeakers Hall- Most medium to large organizations have a Legal department as well as an IT, and hopefully an IT Security department. Sometimes these two departments are blissfully unaware of each other's existence. Sometimes one has complete control over the other. Each of these scenarios represents an extreme and is simply bad for business. This talk will give real-life examples of how this miscommunication can affect your organization, and how both groups can find common ground to start working together.LegalWhereSpeakers Hall
- 15:15 - 15:30
Breather
Take a breather and get ready for the rest of the afternoon!Social NetworkingWhereMain Venue Area  15:30 - 16:15
15:30 - 16:15Incident Response & Threat Hunting Using Bro/Zeek Data
By Mayur Mohan Kaura Sales Engineer, Corelight IncTalk includes Advance Attack Lifecycle and How Zeek/Bro data (open source) can help organizations quickly investigate incidents as well as hunt proactively from network perspective. Zeek/Bro exist since 25 years and provides rich set of logs tailored for Incident responders and threat hunters that is much faster than PCAP based analysis and much richer in contest over netflow logs. This session is for Cyber Security professionals who really want to: Adopt a strong Network Security Monitoring Posture into their existing Response Framework; Save time within their incident response process toggling among various set of existing logs generated from firewall, web, host, DNS, DHCP, etc; Start or enhance their threat hunting posture with a simpler solution "Zeek/Bro".Bro/ZeekData AnalysisNetwork SecurityThreat HuntingWhereSpeakers Hall 16:15 - 17:00
16:15 - 17:00Implementing and Analysis of JA3 data for TLS Fingerprinting using Bro/Zeek Data
I was implementing JA3 (open source from salesforce) for a complex environment to show the value of TLS fingerprinting for network security detection. My approach is hybrid since I was mixing data from network (using open source Bro) and data collected from host (A commercial EDR) to map every JA3 to a process name. My end game is to create a whitelist of JA3 (mainly baseline the use of TLS in our environment) that could be help security monitoring to detect new TTPs as Domain fronting. I already presented some of my research internally and It is the first time to present it outside.ATT&CKBro/ZeekIncident ResponseThreat HuntingWhereSpeakers Hall 17:00 - 17:45
17:00 - 17:45How did you get in my car? A fireside chat covering all the basics of cybersecurity and your automobile
By Coreen Bouchard Founder of PureLogic IT, Robert LealeIt is a herculean task to protect yourself from unknown cyber threats and your car is no different. In this exciting Fireside Chat, Robert Leale, founder of CanBusHack, and Coreen Bouchard, a cybersecurity industry specialist, will discuss the current state of cyber-security in automotives. Some of the key topics they will explore during this Fireside Chat: How to borrow a car in 60 seconds; The importance of car hacking; Best practices and resources; A deep dive into vehicle data reverse engineering and the work Robert has been involved with the Car Hacking Village.AutomotiveReverse EngineeringWhereSpeakers Hall
Day 2
- 08:00 - 09:00
Registration and Networking
Registration and open networking will be between 8am and 9am on days 1 and 2. If you registered on day 1 then you can freely enter the venue without registering again on day 2.Social NetworkingWhereMain Venue Area - The proliferation of IoT devices deployed in homes is increasing because of the utility they can provide. They can give users the facility to perform different tasks just using their smart phones. Users can receive alerts, monitor or change the state of a device. For instance, they can turn on/off lights/appliances, (un)lock padlocks or door locks, monitor environment, and many other actions available for the user depending on the device purpose. However, since IoT devices need to provide ease of implementation, they use discovery protocols, and because of that, they put smart homes at risk to be attacked, even by people without technical knowledge. We performed some empirical studies which have shown us why discovery protocols need to be restricted in a smart home environment. Our research also allowed us to define a threat model to help us to define and propose a possible solution to protect smart homes.Internet of ThingsNetwork SecuritySmart HomesWhereSpeakers Hall
- 10:00 - 10:15
Coffee Break
Perk up and have a snack!Social NetworkingWhereMain Venue Area  10:15 - 11:00
10:15 - 11:00The What, Who, Whom and Why about a Vulnerability Management Program
Traditional vulnerability management is not about pentesting network, apps, or even red/blue/purple team. In today’s world, we need to talk about a Vulnerability Management Program (VMP); a program that puts all the pieces together in order to achieve a more resilient state. While this is not a technical talk, we will cover some of the challenges that other people in the VM-world face daily. This talk will make clear the connection between the VMP and Patch Management, Change Management, Currency Management, Risk Management, Risk Appetite, and others.Vulnerability ManagementWhereSpeakers Hall- Can I speak to the employee base that completes this task? Assessments performed may often overlook how technologies and applications are used within their respective operating environments. By outlining a few case examples lets take a quick journey into identifying, attacking and detecting business process related vulnerabilities. Stop relying on those vulnerability scanners!MisconfigurationsPentestingWhereSpeakers Hall
- 12:00 - 13:00
Lunch
For paid ticket holders lunch will be served.Social NetworkingWhereMain Venue Area - Shodan began as a pet project of John Matherly to scan the internet for specific ports and gather data related to these ports. Since its launch in 2009 Shodan has gained notoriety in the recent years on becoming the go to source to analyze data gathered by Shodan by scouring the internet. Shodan crawls the internet regularly and stores data gathered for analysis by researchers, whitehats and blackhats. Anyone can subscribe and run queries against Shodan database by paying few hundred dollars as subscription fee. Shodan has made it very easy for anyone to gather reconnaissance data without actually doing any reconnaissance, moreover by not engaging directly with the target in reconnaissance phase there is no chance that target would be tipped. By using this information an attacker can easily create a profile for the target and launched targeted attacks on the target. The Author wanted to explore the risk associated with information exposed over the internet and readily available on Shodan for Ottawa Region. We hope that this presentation informs our audience, businesses and government on risks associated with exposing certain ports, services and unsupported software over the internet.Data AnalysisShodanWhereSpeakers Hall
 13:45 - 14:30
13:45 - 14:30Security Groups Speak a Common Language: MITRE ATT&CK
By Suraj Sahu Technical Lead - Threat Research, Trend Mirco, Pawan Kinger Blue Teamer!, work at Trend MicroIn a SOC, triaging alerts generated by Deployed Security products is a tier 1 job for an analyst. The threat intel, analysis and defences (security products) use different severity, message for the same incident, which complicates the security Analyst’s job in Alerts Triage. MITRE has simplified the work of security Analyst and Security Managers with the new ATT&CK Framework. Industry-wide acceptance of the MITRE ATT&CK Framework has enabled security product vendors to integrate it into their product line. MITRE ATT&CK Framework also enables the security vendors to evaluate their products against various TTPs as used by an adversary in an attack chain. In this session, we would like to go through how MITRE ATT&CK Framework will enable security Analyst to act fast and correlate the different Alerts to single Attack Chain and let's see in doing so if we identify any campaign activity. Fun times threat hunting with a common language.ATT&CKBlue TeamKill ChainThreat HuntingWhereSpeakers Hall- It doesn't take one exploit to hack the kingdom. This is a true story about finding multiple different web exploits and chaining them together to compromise an application and discussing the importance of actively monitoring for vulnerabilities and the downsides of letting them going unpatched.Application SecurityKill ChainPentestingVulnerability ManagementWhereSpeakers Hall
- 15:15 - 15:30
Breather
Take a breather and get ready for the rest of the afternoon!Social NetworkingWhereMain Venue Area - If you're responsible for a security program or are expected to lead the last line of defense against the onslaught of relentless risks - we need to talk. When a new attack class appears do you know what it means for your security? When you're asked for 2020's security priorities how do you answer the inevitable question: "So what?" When a new product is buzzing around halls of R&D how do you know where it fits in *your* security priorities? This talk looks at the journey of being handed the keys to an information security program. We'll discuss our journey from controls-based SP800-53, to Maturity Models like BSIMM and ultimately deciding on Wardley Mapping for providing long-range guidance and short-term priorities to hundreds of technical staff across multiple continents developing national-security level software. Wardley Mapping is a new technique for communicating situational awareness. Get good at this and you'll find yourself in the middle of everything from business to technical strategy.WhereSpeakers Hall
- Ever wonder why some vulnerabilities are never fixed? Ever had the thought of "how come is this still present.... it's just a click!"? Well, in this talk, we will cover some of the challenges that organizations face when attempting to fix some vulnerabilities, in other words... what happens after a pentest report is submitted.PentestingVulnerability ManagementWhereSpeakers Hall
 17:00 - 17:45
17:00 - 17:45Closing Keynote - “Insider Secrets” to HOW hackers are getting in, and WHY
By Terry Cutler Cyology LabsThis session will show attendees a “behind the scenes look” at how hackers harvest as much information on you before launching a targeted attack. At the end of this talk, the audience will be more alert as to what they’re posting online and how it can be used against them. Topics include:- The problem with modern day security
- The phases hackers use to target you
- Social Engineering awareness
- Real-World hacking demonstration
- Defensive tools
Kill ChainSocial EngineeringWhereSpeakers Hall